Obsah
Griffteam
Veřejná IP: 80.95.100.114
Servery
Fyzické
HPLX06
XEN
HPLAPP01 - účetní server - Libor
HPLAPP02 - instalace - Lukáš
DCGRIFF - řadič domény
root@hplx06:~# xl li Name ID Mem VCPUs State Time(s) Domain-0 0 4096 2 r----- 2635904.6 vssql01 10 10240 4 -b---- 856332.7 dcgriff 13 8192 4 -b---- 176496.4
HPLX01
ProxMox
Proxmox URL: https://192.168.10.93:8006
root@hplx01:/usr/local/sbin# qm list
VMID NAME STATUS MEM(MB) BOOTDISK(GB) PID
100 VSSQL04 stopped 4096 40.00 0
101 VSSQL03-OLD running 8124 300.00 5012
102 VSSQL02 running 8124 560.00 5095
103 VSSQL05 running 32768 560.00 5389
104 VSSQL01 stopped 8192 500.00 0
105 VSSQL03 running 8192 450.00 4937
HPLX02
PROXMOX - Jira, Bamboo, Bitbucket, Confluence
Proxmox URL: https://192.168.10.98:8006
root@hplx02:~# pct list VMID Status Lock Name 110 running jira 111 running bamboo 112 running confluence 113 running bitbucket
HPLX03
Do managementu Raid controlleru z menu po boot systému libovolnou klávesou. Pak přes F8
XEN
root@hplx03:~# xl li Name ID Mem VCPUs State Time(s) Name ID Mem VCPUs State Time(s) Domain-0 0 4094 2 r----- 1213024.7 hplapp01 20 6144 4 -b---- 1094717.2
HPLX05
XEN
root@hplx05:~# xl li Name ID Mem VCPUs State Time(s) Domain-0 0 2947 2 r----- 107000.0 hplsvn 1 1024 2 -b---- 213213.2 unifi 2 2048 2 -b---- 429026.9 bugzilla 3 2048 2 -b---- 58847.6
Virtuální
DHCP
Dhcp službu v lokalitě Jičínská zajištují dva servery v režimu failover.
https://www.madboa.com/geek/dhcp-failover/
Jedná se o servery hplx03 a hplx05. Kde hplx03 je nastaven jako primární server.
IP rozsah:
range 192.168.10.101 192.168.10.160; range 192.168.10.175 192.168.10.220;
IPSEC Bratislava
Lokální IP: 10.0.49, 10.0.0.50 a testovací server 10.0.0.66 adresy v Bratislavě - lze na ně pingnout - např. z VSSQL02 nebo přímo z MK.
ping 10.0.0.50 interface=bridge
UPS
APC 1000VA
Management na HPLX06
Připojené servery:
- HPLX06
- HPLX03
CyberPower 1500VA
https://www.cyberpowersystems.com/product/software/power-panel-personal/powerpanel-for-linux/
pwrstat -status
pwrstat -config
pwrstat -pwrfail -delay 180 -active on -cmd /etc/pwrstatd-powerfail.sh -duration 60 -shutdown on pwrstat -lowbatt -runtime 300 -active off -cmd /etc/pwrstatd-powerfail.sh -duration 10 -shutdown off
root@hplx01:/home/snemec# pwrstat -config
Daemon Configuration:
Alarm .............................................. On
Hibernate .......................................... Off
Action for Power Failure:
Delay time since Power failure ............. 180 sec.
Run script command ......................... On
Path of script command ..................... /etc/pwrstatd-powerfail.sh
Duration of command running ................ 60 sec.
Enable shutdown system ..................... On
Action for Battery Low:
Remaining runtime threshold ................ 300 sec.
Battery capacity threshold ................. 35 %.
Run script command ......................... Off
Path of command ............................ /etc/pwrstatd-powerfail.sh
Duration of command running ................ 10 sec.
Enable shutdown system ..................... Off
Management na HPLX01
Připojené servery:
- HPLX01
- HPLX02
- HPLX05
- Firewall - mail.hpl.cz
- BckServer
WIFI UNIFI
Unifi controller
URL: https://192.168.10.55:8443/
2 x AP talire, jeden umisten v chodbe - APUNIFI01 IP: 192.168.10.12, druhé AP je v kanceláři v prvním patře APUNIFI02 IP: 192.168.10.13
Tiskárna
Konica Minolta Bizhub C227
URL: http://192.168.10.50/wcd/system_device.xml
Exchange server
Exchange Server 2013
Fyzický server HPLX03(HP)
Při změně konfigurace diskového řadiče je potřeba nejdříve po výzvě stisknout libovolnou klávesu(Option Rom) a pak po identifikaci disk řadiče stisknout kl. F8
Pozor, jedná se až o druhou nabídku na stisknutí F8.
How to dump the contents of an IPSec tunnel on StrongSwan with tcpdump
https://7layers.semperen.com/content/how-dump-contents-ipsec-tunnel-strongswan-tcpdump
http://ithitman.blogspot.com/2012/05/how-to-decrypt-ipsec-packets.html
tcpdump -i any -nn esp -w /tmp/ipsec.pcap
ip xfrm state
src 195.168.26.74 dst 80.95.100.114
proto esp spi 0x3c47750f reqid 16385 mode tunnel
replay-window 32 flag af-unspec
auth-trunc hmac(sha1) 0x69b70f1f2b59fb99b52a1402e1c89df21afe5670 96
enc cbc(des3_ede) 0xecfe85280f0dcee7839e9aa408e095e2cec179ca07e3e1ed
src 80.95.100.114 dst 195.168.26.74
proto esp spi 0x773bb618 reqid 16385 mode tunnel
replay-window 32 flag af-unspec
auth-trunc hmac(sha1) 0x87a564781da8c8d0ce72a9b089d30ecc49906232 96
enc cbc(des3_ede) 0x31877283c645345b0676e8396738086a06dce3732d9512e6
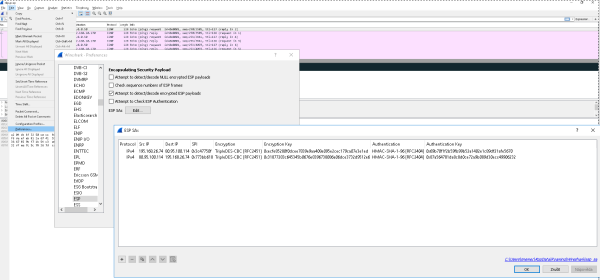
Dekódování ESP provozu pro WireShark
https://cookbook.fortinet.com/decrypting-esp-payloads-using-wireshark-56/
# This file is automatically generated, DO NOT MODIFY. "IPv4","195.168.26.74","80.95.100.114","0x3c47750f","TripleDES-CBC [RFC2451]","0xecfe85280f0dcee7839e9aa408e095e2cec179ca07e3e1ed","HMAC-SHA-1-96 [RFC2404]","0x69b70f1f2b59fb99b52a1402e1c89df21afe5670" "IPv4","80.95.100.114","195.168.26.74","0x773bb618","TripleDES-CBC [RFC2451]","0x31877283c645345b0676e8396738086a06dce3732d9512e6","HMAC-SHA-1-96 [RFC2404]","0x87a564781da8c8d0ce72a9b089d30ecc49906232"
Na obrázku je již dekódovaná komunikace v IPSEC kanálu, hodnoty dosazeny z výstupu příkazu ip xfrm state